
On a Friday afternoon early in July, I was pleased to hear the ABC’s current affairs radio program PM cover cyber-security in the small business sector. It’s impossible for a four-minute radio spot to be comprehensive, but building awareness is a slow process.
To kick off what I hope will be an ongoing discussion of security in the solar energy world, I’d like to focus on introducing some of the things a homeowner needs to consider if their household solar power system is connected to the Internet.
The PM segment can be heard here, and in it, UNSW Canberra Cyber’s Nigel Phair (a well-known expert) asks a handful of useful questions as a starter for cyber-security:
- How tech-heavy is your business? (Or, since I’m thinking of household PV here, how tech-heavy is your home setup?)
- Where is the data kept?
- Who has access to that data?
- Why do they have access?
Solar energy equipment is very tech-heavy and getting more so, making Phair’s last three questions just as relevant to the PV owner as to the small businesses he had in mind.
Where is the data?
If you recall the kinds of setups we’ve discussed here and here, to try and implement solar energy diversion if it’s not built into the system, you’ll quickly see the answer to “Where is the data kept?” is “All over the place”; which isn’t ideal from a security point of view.
The solar inverter (or a data logger attached to it) collects and stores data; it’s connected to the Internet through a household broadband modem; the data is sent to a cloud service (either operated by the vendor, or a third party service) where it’s stored and formatted for presentation. Another system accesses that service to get a local copy of the data for decision-making (“Is there enough power in the PV system to charge the EV?”) and yet another API accesses the data for a mobile app; and so on.
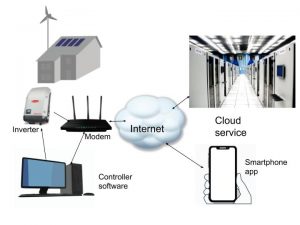
A modern solar power system is exposed to internet in many ways. That means you need to consider its cyber security.
Who has access?
For most or all the hardware and software in this image, usernames and passwords are the default for controlling who can access the data.
At the very minimum, everything with an Internet connection must be protected by a strong password, with a password manager – Apple’s Keychain or a browser-based service like LastPass – so you don’t have to remember “haJd#M4n67x*%”.
Take the broadband modem for example: the usual default admin password is often “admin”. If an attacker logs into the modem, they’ll have a path to whatever connects the inverter, and worse, they can start poking around the control system.
Everywhere there’s a password, make it a strong one, and you can also ignore the ancient (and now superseded) warning to change your passwords regularly. Nobody’s going to mount a successful “dictionary attack” (using a fast computer to test one word after another) against a properly random password.
The same goes for any smartphone app you use: give it a strong password.
Likewise, if your reseller or solar installer has access to the system (for example, to help with fault-finding), make sure they also use strong passwords.
Phishing and ransoms
Something Nigel Phair didn’t mention is the popular form of attack known as ransomware: the criminal breaks into a victim’s PC, encrypts it, and demands a ransom from the owner to let them have their system back.
On a large scale, this can be utterly catastrophic – the criminals behind an attack a couple of years ago called “NotPetya” caused hundreds of millions of dollars damage to the global shipping giant Maersk (I wrote about it in a previous life with UK IT publication The Register here).
But it isn’t just about big business: it would be devastating if your PV system was locked up by ransomware.
The usual attack channel for ransomware is “phishing” via e-mail: you get a legitimate-looking message (“click link to view invoice”), and the link downloads the malware that attacks your computer.
The first and most obvious advice is one I’ve heard repeated for two decades as an IT journalist: don’t click on links in e-mails. Since phishing still works, it’s pretty clear that people still don’t follow this advice; so I’d suggest that for something as important as control software, you don’t use the same to check e-mail as well.
There’s still a risk, though: someone might get tricked on their laptop, and the malware is able to jump to other machines on the same network – get good virus and malware protection, and keep it updated
If your computer is doing important work like helping control where your solar power goes, I strongly recommend getting advice about malware protection, and following that advice.
Backup is your friend
In most cases, the setup in my badly-drawn diagram isn’t going to generate huge amounts of data, so a simple 1 Terabyte portable hard drive from your local office supplies shop will easily provide backup. If you do fall prey to something like ransomware, you won’t have to panic, because you can restore the whole system from the backup.
Since a professional malware attacker will also try to encrypt the backup, you need a bit of hygiene here: unplug the backup drive when it’s not in use.
Encryption is for everyone
A couple of final thoughts for this article on protecting information with encryption.
Encryption is an absolute must for any important data travelling over the Internet. A good example is if you’re using the smartphone app to check your solar power system, and you’re connected to a public Wi-Fi hotspot. If your data isn’t encrypted, it’s easy for someone connected to the same hotspot to view your communications – and maybe discover your usernames and passwords.
The good news here is most services you’ll work with will encrypt their data by default. The important thing for you is to check that a service is safe, and in a Web browser, that’s easy – just take a look at the URL.
This article, for example, travelled from SolarQuotes to you using an encrypted channel. The HTTPS:// in the URL means it’s using “HTTP Secure” – the server encrypts the data before sending it to you, and your browser decrypts it.
Your modem has a web page for configuration – it’s vital that it uses HTTPS after you’ve logged in. Likewise, make sure any cloud service you connect to uses HTTPS.
In this article, I’ve focused on end-user concerns – and still barely scratched the surface! When I revisit solar power system security in the future, I’d like to look at it from the retailer and reseller point of view – so I’ll welcome anyone raising questions they’d like answered.

 RSS - Posts
RSS - Posts


Data security is becoming an issue that should be considered, especially with the stories of Huawei getting out there. Enphase Energy uses the Amazon Web Services cloud. Not sure about SolarEdge from Israel, APS, Hoymiles, ABB, Fronius, SMA… It would be nice to have a quick list of where the server data is held.
Luckily, for Enphase, their communication gateway is not necessary for the solar solution to work. I keep mine off a lot, and just turn it on when I want to do a quick check-up on my solar system. However, with the advent of storage, the Envoy is needed for the solution, but still the cloud may only be needed to access monitoring data.
Is it possible for a hack to shut down all the inverters for a particular company? Who knows?
.. or maybe just causes nuisance outages by turning off inverters, or nudging their peak output down by a few percent during anticipated periods of high demand.
Industrial espionage in the era of smart connected inverters.
Mesg to Admin. I post as user “Stewart” here. Often when I post it states “Slow down you are posting to fast” (or words to that effect). Then if I try again it states “You have already said that” and returns me to the top of the page with no post is waiting for moderation message. Very frustrating.
over and over and over again: —> KISS!
…. and always remember:- Y’can’t beat Big Brother at his own game.
Funny this article came out today – I was at my dads place and looking for a wifi network and bingo, up pops someones ZeverSolar inverter, plain as day for any hacker to try and crack into. Dad has a solar system too, but it uses Solar Analytics which doesn’t use wifi but instead uses 4G. His network is invisible as a result.
first of all manufacturers should turn off by default any web activity of their products. for example my newly installed SMA chinese made SBx.0 frantically tried calling home to germany when wifi was present. luckily I blocked it in my router.IOT they call it. I(DI)OT is a better name.
Well, there is a simple solution to all of this (at least the way I see it) which is to select a solar inverter which allows the date to be collected locally (such as my Fronius Sumo) and then turn off it’s option for sending data to their cloud server. For added piece of mind, block it from accessing the web and you are done.
How do you view your data? Access the inverter using local ‘rest’ service calls and create nice graphs in Home Assistant. Winning.
I’ve had a Huawei inverter installed (yes those guys), turns out their advertised “wifi monitoring” feature is a data logger that’s hardcoded to their own cloud service on AWS, and i would access it on my phone app via a shared tenancy portal. And of course the sales rep failed to mention any of this! When i quizzed Huawei about getting my own software to host in my own network because, frankly i don’t trust them, the answer came in the form of a software quote. Needless to say that’s a negatory for me. Now I’m exploring options of using my own RS485 IoT, running my own source code, to collect data from the inverter. I can probably write better looking dashboard and reports anyway. Problem however is that, they don’t like publishing their RS485 protocol specs and they don’t really conform to standard ones either. Project status: impasse, to be continued.
SolarX has absolutely no security. You can connect to inverter without a password. What a joke.
I found it very interesting you suggested using https after logging in. So use in insecure connection to enter your credentials?
Obviously, none of you have heard of CA Rule 21 which will allow utilities to control your PV system.
What the author does not fulky understand is that monitoring is not required for PV system operation. Neither is any PC connection required even when charging an EV. There is no communication that “diverts” electricity to the EV. It is diverted by physics.
Monitoring data is only one way communication for most installed systems. Having access to the data or data stream does not mean control of the PV system.
Now, if you have a smart system with PV usage control, you night have some communication between the PV inverter and the EV charger, but it still would not be externally accessible nor use a PC.
GREATER than 99% of all residential systems Installed are safe from remote hacking. All new systems that meet CA Rule 21 Phase 3 requirements are at risk for remote hacking, which, in 10 years, may be a significant number to pose a rush to the grid. Maybe.
Great reply. “What the author does not fully understand is that monitoring is not required for PV system operation. Neither is any PC connection required even when charging an EV. There is no communication that “diverts” electricity to the EV. It is diverted by physics.” … it’s coming. IQ8 Ensemble will be able to divert energy to the phase that needs it most, so the intelligence is getting more intricate.
Monitoring is not required now for Enphase solar PV systems, but add Encharge storage to the mixture, and Enphase’s Ensemble will require a communications gateway aka Envoy. With my M215/M250-series system, II shut my Envoy off for extended time periods, then turn it on to see how every micro is doing, and the energy I’ve produced for the day, week, month, year. For me, monitoring is crucial to pinpointing problems with a panel/microinverter, and then being able to easily fix it yourself.
Cheers, man and to Finn, Ronald and Richard! You guys are in the Land Down Under where women glow and men plunder! Always wanted to go there…
“unplug the backup drive when it’s not in use”
–
it might be a good idea to unmount any drive before unplugging it.
As a general rule, to store anything personal at all on the ‘cloud’, or rely on business services (eg. accounting, tax, invoice processing and debtors statements etc) provided via the cloud for your business; verges on lunacy in my opinion.
Heres a link that summarises 9 major security issues:
https://www.skyhighnetworks.com/cloud-security-blog/9-cloud-computing-security-risks-every-company-faces/
A more indirect situation is the case where (say) a firm provides (say) accounting services to your business, and stores your data, along with those of all their other clients, on a ‘cloud’ server. That too is just as risky.
Basically the ‘cloud’ is a giant honey-pot for hackers. No longer do they need to hack hundreds of millions of sites individually, just pick a few hundred or so cloud-based sites and focus on them, and they’re all conveniently located at the one place.
CyberSecurity is a vast field, with numerous sub-specialties, only just two of which are the issues surrounding personal ‘privacy’ and ‘identity theft’. On a personal level there’s a few simple precautions you can take which can minimize the amount of damage you’ll suffer if you get ‘hacked’.
A good starting question to ask yourself is: What are the potential consequences for me if some-one stole my laptop?
(thus enabling them to hack it at their leisure) and to make it even worse, also took the notebook in the drawer of the desk it sat on which contains all the passwords you’ve so carefully written down.
There are some useful free tools around that people can use to ‘protect’ themselves to some degree, one starting point is the Electronic Freedom Website at: https://www.eff.org/
The rest of it is largely the responsibility of the individual – if you decide to keep on using ‘obvious’ passwords (despite the well publicized limitations of doing so), …. if you can’t be bothered to read the instruction manual for your router and set up a new password… etc etc… well… you won’t get a lot of sympathy these days.
From what I’ve read recently, about 50% of Australians now use encrypted VPN services for their internet services. However some 10% of internet users actually don’t use any passwords at all on their home device, and presumably they’re most likely among the non-VPN users. (technically there is a password except its termed as ‘blank’ )
The world has moved on a bit too. Nowadays hacking is more ‘indirect’ – the starting point is more often ANY peripheral device that’s attached to the computer, because the security on those is usually pretty weak and they are (in a sense) a ‘user’ of your main system with access to it.
Here’s a link to a 2017 article regarding ‘smart home devices’ such as Amazon Alexa and Google Home which seems still quite relevant to-day: https://nakedsecurity.sophos.com/2017/01/27/data-privacy-day-know-the-risks-of-amazon-alexa-and-google-home/
It is a good idea to wire connect your devices with network cabling using the ports on your router where you easily can.
Hi, You Guys all know so much about the risks of internet hackers and I guess there must be a real threat to be so up on the subject. We have a residential solar setup installed in June 2018 including 18 panels and hot water connected to an LG battery unit,that we monitor our production output/consumption online via the home PC. Do we need to be careful at this stage when going online to monitor that info?
Thanks, just learning about cyber security so it’s a little overwhelming…
I designed over 2000 WANs via the IT company I founded in the late ’80’s until I retired a few years back. We lost the security debate in the mid ’90’s as the powers that be “could not see the point”. So nowadays I can control my mates Jeep remotely into the nearest ditch… progress?
Also, wi-fi / 4g / 5g / wireless anything is being overused these days way past any sanity point – and they are not really secure. Example – my microinverters use cables to transfer the power (obviously) so why on earth is the only monitoring supposed to be done via wireless? Dudes, the cable is already there… Don’t get me started on “wireless video surveillance cameras” that presumably also get powered by mains electricity. Add “smart TVs” and “amazon / google home” devices with voice recognition that connect to the internet – you must be joking, ever heard of privacy?
I now have two networks at home now – one for all my critical items and one which I use to connect to the internet via NBN – like my landline and this computer for emails / browsing. The twain will never meet.